- Posted on
- admin
- No Comments
What is AMI in AWS
Introduction
What is Cloud Computing? (brief overview)
Cloud computing refers to the on-demand delivery of IT resources – servers, storage, databases, networking, software, analytics, intelligence, and more – over the internet. These resources are offered as services, eliminating the need for physical infrastructure management and upfront capital expenditure. Cloud computing provides scalability, flexibility, and cost-efficiency, allowing businesses to adapt to changing demands and focus on their core competencies.
Unveiling the Power of Amazon Web Services (AWS)
Amazon Web Services (AWS) is the world’s leading cloud computing platform, offering a comprehensive suite of on-demand services to build, deploy, and manage applications on a global, scalable infrastructure. AWS encompasses a vast range of services from compute, storage, and databases to networking, analytics, and artificial intelligence. Its pay-as-you-go pricing model eliminates the need for upfront investments in hardware and software, making it an attractive option for businesses of all sizes.
Introducing AMIs: The Building Blocks of Your Cloud Infrastructure
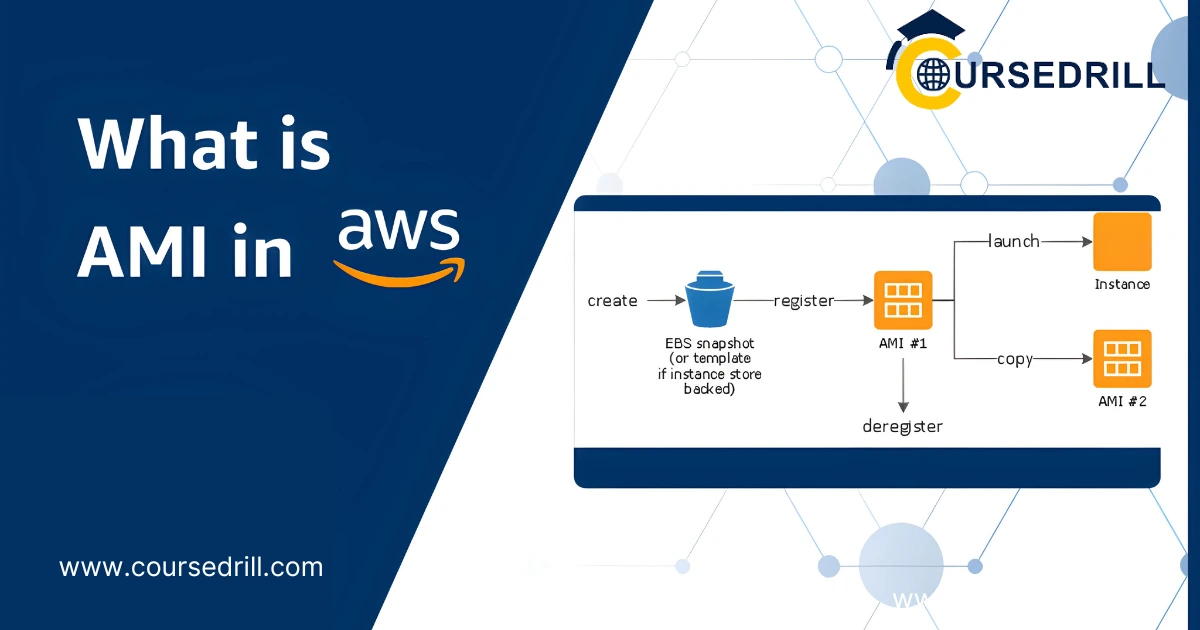
Amazon Machine Images (AMIs) are the fundamental building blocks for creating and deploying infrastructure on AWS. An AMI is a template containing the operating system, applications, and configurations required to launch an instance – a virtual server running in the AWS cloud. AMIs offer consistency and repeatability, enabling you to quickly provision identical instances with pre-configured settings, streamlining your deployments and ensuring efficient resource utilization.
Decoding the Anatomy of an AMI
An AMI acts as the blueprint for your cloud infrastructure, defining the essential components that come pre-configured when you launch an instance. Understanding the core elements that make up an AMI is crucial for effectively utilizing and customizing them for your specific needs.
Core Components
An AMI comprises three key components that work together to define the state of a launched instance:
- 1. Operating System (OS): This forms the foundation of your instance, providing the core functionality for managing hardware resources, running applications, and interacting with users. Popular operating systems available as base images for AMIs include Amazon Linux 2, Ubuntu, Windows Server, and more. The choice of OS depends on your application requirements and preferences.
- 2. Applications: AMIs can be configured to include pre-installed applications, eliminating the need for manual installation on each instance. This can encompass web servers, databases, development tools, or any software needed for your application to function. Including essential applications within your AMI streamlines deployment and ensures consistency across your infrastructure.
- 3. Configuration Files: These files define settings and customizations specific to your needs. Configuration files can manage various aspects such as user accounts, security settings, application-specific configurations, and scripts to automate tasks during instance launch. Effectively using configuration files allows you to tailor your AMI to your environment and automate repetitive tasks.
Understanding Root Device and Block Devices
An AMI also defines how storage is allocated to your instances. There are two primary categories of storage devices to consider:
- Root Device: This is the primary storage device where the operating system and its core applications reside. The root device typically utilizes an Elastic Block Store (EBS) volume, offering persistence and allowing you to store data that needs to survive instance restarts.
- Block Devices: AMIs can define additional block devices attached to the instance. These can be EBS volumes for additional storage needs or instance store volumes for temporary data that gets lost upon instance termination. Specifying block devices within your AMI allows you to configure the storage capacity and type required for your applications.
Unveiling the Different Types of AMIs
The diverse landscape of AMIs in AWS caters to a wide range of deployment needs. Understanding the various types available empowers you to select the most suitable option for your specific requirements.
AWS Marketplace AMIS: Pre-built Solutions for Common Needs
The AWS Marketplace offers a vast library of pre-configured AMIs from software vendors and partners. These AMIs provide a convenient way to deploy popular applications and pre-built servers, saving you time and effort compared to building them from scratch.
Benefits of Using Marketplace AMIs:
- Faster Deployment: Marketplace AMIs eliminate the need for manual configuration and application installation, accelerating your deployment process.
- Pre-validated Solutions: Many Marketplace AMIs are pre-validated by the vendors, ensuring compatibility and functionality with their software.
- Variety and Choice: The Marketplace offers a vast selection of AMIs catering to diverse use cases, from web servers and databases to development tools and security solutions.
Exploring Popular Categories of Marketplace AMIs:
- Web Servers: Find pre-configured AMIs with popular web servers like Apache, Nginx, and IIS, ready to host your web applications.
- Databases: Deploy AMIs with pre-installed database software like MySQL, PostgreSQL, and Oracle Database, streamlining your database infrastructure setup.
- Development Tools: Utilize AMIs pre-configured with development environments and tools like Java Development Kit (JDK), Node.js, and integrated development environments (IDEs).
- Security and Compliance: The Marketplace offers AMIs tailored for specific security and compliance needs, adhering to industry standards like PCI DSS and HIPAA.
Amazon-provided AMIs: Reliable Foundations for Your Deployments
Amazon offers a collection of free-to-use base AMIs that serve as a solid foundation for building your own custom AMIs. These AMIs provide a clean and up-to-date operating system environment without any additional software pre-installed.
Understanding the Use Cases for Amazon-provided AMIs:
- Customization: These AMIs are ideal for building custom AMIs tailored to your specific needs, allowing you to install and configure the required applications and settings.
- Control and Security: Amazon-provided AMIs offer greater control over the instance environment, ensuring you have a clean and secure starting point for your deployments.
- Cost-effectiveness: These base AMIs are free to use, minimizing infrastructure costs compared to some Marketplace AMIs with licensing fees.
Common Examples of Amazon-provided AMIs:
- Amazon Linux 2: A free, open-source Linux distribution optimized for running on AWS.
- Ubuntu: A popular, free, and open-source Linux distribution offering a wide range of software packages.
- Amazon Red Hat Enterprise Linux (RHEL): A paid option providing a reliable and supported enterprise-grade Linux distribution.
- Windows Server: A family of Windows operating systems designed for server environments, available with various licensing options.
Community AMIs: Sharing the Power of Collaboration
The AWS community provides a wealth of AMIs shared by other users. These AMIs can offer unique functionalities or cater to specific niche use cases.
Advantages of Utilizing Community AMIS:
- Cost-effective: Community AMIs are often free to use, potentially reducing your infrastructure costs.
- Innovation and Customization: These AMIs can offer pre-configured environments for specific tasks or integrate with unique tools and technologies.
Important Considerations When Using Community AMIs:
- Security and Trust: Community AMIs come from various sources, so it’s crucial to assess the reputation and security practices of the provider before using them.
- Support and Updates: Community AMIs may not have readily available support or receive consistent updates, potentially impacting their reliability.
- Quality and Functionality: The quality and functionality of community AMIs can vary, requiring careful evaluation before deployment.
Crafting Your Own Custom AMIs: A Step-by-Step Guide
Building custom AMIs empowers you to tailor your AWS infrastructure to your specific needs. This section delves into the step-by-step process, equipping you with the knowledge to create robust and efficient AMIs.
Prerequisites: Setting the Stage for AMI Creation
Before embarking on your custom AMI journey, ensure you have the necessary prerequisites in place:
- AWS Account: An active AWS account is essential for accessing and utilizing AWS services like EC2 and S3, which play a crucial role in AMI creation and storage.
- IAM Permissions: Assign appropriate IAM permissions to the user or role creating the AMI. These permissions should allow launching EC2 instances, creating Amazon S3 buckets (for storing temporary files during the build process), and creating AMIs.
- Familiarity with Linux Commands (if applicable): While some tools can automate tasks, basic familiarity with Linux commands can be helpful for navigating the build process, particularly when using Amazon-provided Linux base AMIs.
Choosing the Right Base Image: Selecting the Foundation
The base image serves as the starting point for your custom AMI. Here’s what to consider when making your selection:
- Operating System: Choose an operating system that aligns with your application requirements and technical expertise. Consider factors like compatibility with your software, security posture, and familiarity with package management tools.
- Amazon-provided AMIs vs. Marketplace AMIs: For complete control and customization, opt for an Amazon-provided base AMI. If you need pre-installed software or specific configurations, explore relevant Marketplace AMIs, keeping licensing costs in mind.
- Version Compatibility: Ensure the chosen base image version is compatible with the applications you plan to install and the overall architecture of your deployment.
Installing and Configuring Applications
Once you have your base image, it’s time to install and configure the necessary applications. Here are some key considerations:
- Package Management Tools: Utilize the appropriate package manager for your chosen operating system (e.g., yum for Amazon Linux 2, apt for Ubuntu) to efficiently install software packages.
- Configuration Management Tools: Consider using infrastructure as code (IaC) tools like Terraform or Ansible to automate configuration management tasks and ensure consistency across your AMIs.
- Security Best Practices: Adhere to security best practices throughout the configuration process. This includes installing security updates, configuring user accounts with appropriate permissions, and disabling unnecessary services.
Automating the Build Process with AWS Tools (e.g., Packer)
Manually building AMIs can be time-consuming and error-prone. AWS offers tools like Packer that streamline the process. Packer allows you to define a template specifying the base image, applications to install, and configuration steps. This template can then be used to automate the AMI creation process consistently and efficiently.
Benefits of Using Packer:
- Repeatability: Packer ensures consistent builds across different environments, minimizing the risk of errors.
- Scalability: Easily scale your AMI creation process by running Packer builds in parallel or integrating them into your CI/CD pipeline.
- Version Control: Manage your Packer templates in version control systems, allowing you to track changes and revert to previous configurations if needed.
Optimizing Your Custom AMI for Efficiency
Once you have a functional custom AMI, consider optimization techniques to enhance its performance and minimize costs:
- Minimize Installed Packages: Only install applications essential for your use case. Unnecessary packages increase the AMI size and can introduce security vulnerabilities.
- Clean Up Temporary Files: Remove any temporary files or logs generated during the build process to reduce the final AMI size.
- Use Appropriate Instance Types: When launching instances from your custom AMI, select the most cost-effective instance type that meets your application’s resource requirements.
Launching Instances from Your AMIs: Bringing Your Infrastructure to Life
Having meticulously crafted your custom AMI, it’s time to leverage it to provision virtual servers in the AWS cloud. This section guides you through the process of launching instances from your AMIs and managing their lifecycle.
Selecting the Right AMI for Your Needs
With a diverse collection of AMIs at your disposal (custom, Marketplace, or Amazon-provided), choosing the most suitable option is crucial:
- Understanding Your Application Requirements: Consider the operating system, software dependencies, and resource needs (CPU, memory, storage) of your application.
- Matching AMI Functionality: Select an AMI that aligns with the intended purpose of your instances. For web servers, choose an AMI with a pre-configured web server like Apache or Nginx. For development environments, consider an AMI with developer tools pre-installed.
- Security Considerations: Choose an AMI built with security best practices in mind. This includes ensuring the base image is up-to-date with security patches and configuring user accounts and permissions appropriately.
Configuring Instance Launch Parameters
When launching instances from an AMI, you can specify various parameters to customize the deployment:
- Instance Type: Select an instance type that provides the necessary resources (CPU, memory, storage) for your application to run efficiently. AWS offers a wide range of instance types optimized for different workloads (compute-intensive, memory-intensive, etc.).
- Security Groups: Define security groups to control inbound and outbound network traffic for your instances. This ensures only authorized traffic reaches your instances, enhancing security.
- Block Device Mappings: Configure additional storage volumes beyond the root device defined within your AMI. This allows you to attach EBS volumes for persistent data storage or leverage instance store volumes for temporary data.
- User Data Scripts: Utilize user data scripts to automate tasks during instance launch. These scripts can be used to install additional software, configure settings, or run custom commands on the newly launched instance.
Understanding Instance Lifecycle Management
Once your instances are launched, it’s essential to manage their lifecycle effectively:
- Instance States: Instances can be in different states throughout their lifecycle, such as “pending,” “running,” “stopping,” and “terminated.” Understanding these states allows you to monitor your instances and take appropriate actions.
- Monitoring and Scaling: Monitor the health and performance of your instances using AWS CloudWatch. You can also leverage auto scaling groups to automatically scale your infrastructure up or down based on predefined metrics.
- Termination and Cost Management: Terminate instances when they are no longer needed to avoid unnecessary costs. Explore AWS features like Spot Instances for cost-optimized deployments, where instances are automatically terminated when the market price exceeds a set limit.
Managing Your AMIs: Keeping Your Cloud Infrastructure Organized
As you create and utilize AMIs in your AWS environment, maintaining organization and efficient management becomes crucial. This section explores best practices for versioning, sharing, and deregistering AMIs to ensure a well-structured and cost-effective cloud infrastructure.
AMI Versioning: Maintaining Control and Consistency
Versioning your AMIs allows you to track changes, maintain control over deployments, and easily revert to previous configurations if necessary. Here are key strategies for effective AMI versioning:
- Clear and Consistent Naming Conventions: Implement a naming scheme that incorporates version information or deployment purpose. This simplifies identification of the specific functionality and configuration of each AMI version.
- Version Control Integration: Consider integrating your AMI build process with version control systems like Git. This allows you to track changes made to the AMI build process and revert to previous versions if needed.
- Testing New Versions: Before deploying a new AMI version to production, thoroughly test it in a staging environment. This ensures compatibility, functionality, and adherence to security best practices.
Sharing Your AMIs with Others: Collaboration within Your Organization
In a collaborative environment, sharing custom AMIs within your organization streamlines deployments and promotes consistent infrastructure. Here’s how to effectively share your AMIs:
- Private AMIs vs. Public AMIs: For internal use within your organization, utilize private AMIs. Public AMIs are accessible to anyone with an AWS account, so exercise caution before making custom AMIs public.
- IAM Permissions: Grant appropriate IAM permissions to users or groups who need to access and launch your AMIs. This ensures controlled access and prevents unauthorized deployments.
- Documentation and Version Notes: Provide clear documentation for your shared AMIs, including details about functionality, configuration changes in new versions, and any specific deployment instructions.
Deregistering AMIs: Cleaning Up Unused Resources
Over time, you may accumulate unused AMIs associated with outdated deployments or experiments. Deregistering these AMIs frees up resources and helps maintain a clean and cost-effective cloud environment.
- Identifying Unused AMIs: Utilize AWS tools like the AWS Management Console or the AWS CLI to identify AMIs that haven’t been launched for a specific period.
- Deregistering Unnecessary AMIs: Once you’ve confirmed an AMI is no longer required, deregister it using the AWS Management Console or the AWS CLI. This removes the AMI from your account but doesn’t delete the underlying snapshot (if applicable).
- Snapshot Management: Snapshots associated with deregistered AMIs can still incur storage costs. Regularly review snapshots and delete those no longer needed to optimize storage utilization.
Security Considerations When Working with AMIs: Building a Fortress in the Cloud
Security is paramount when managing AMIs in your AWS environment. They serve as the blueprints for your infrastructure, and any vulnerabilities within them can be replicated across all launched instances. This section outlines best practices for securing your AMIs, identifying and mitigating potential threats, and controlling access with IAM policies.
Best Practices for Securing Your AMIs
- Hardening the Base Image: Start with a secure foundation. Utilize the latest Amazon-provided AMIs that are pre-configured with security best practices in mind. These AMIs typically have unnecessary services disabled, essential security patches applied, and default user accounts secured.
- Minimize Installed Software: Only install applications essential for your use case. Reducing the software footprint within your AMI minimizes the attack surface and potential vulnerabilities.
- Regular Security Updates: Patch your AMIs regularly to address known vulnerabilities in the operating system and software packages. Consider automation tools to streamline the patching process and ensure timely updates.
- Least Privilege Principle: Configure user accounts with the minimum permissions required to perform their tasks. Avoid using privileged accounts (like root) for everyday operations.
- Secure Storage: Encrypt data at rest within your AMIs and on EBS volumes attached to your instances. This adds an extra layer of protection in case unauthorized access occurs.
Identifying and Mitigating Potential Vulnerabilities
- Security Scans: Regularly scan your AMIs for vulnerabilities using automated security scanners. These tools can identify potential security issues within the operating system, applications, and configurations.
- Vulnerability Assessments: Conduct periodic vulnerability assessments of your overall environment, including your AMIs. Penetration testing can further simulate real-world attack scenarios and identify exploitable weaknesses.
- Staying Informed: Proactively stay updated on security advisories and bulletins from AWS and software vendors. This allows you to address potential vulnerabilities before they are exploited.
- Version Control and Rollbacks: Maintaining version control of your AMI build process allows you to easily rollback to a previous version if a security vulnerability is discovered.
IAM Policies and Permissions: Controlling Access to Your AMIs
- Granular IAM Permissions: Implement IAM policies that define who can create, launch, modify, or share your AMIs. Avoid granting excessive permissions and utilize the principle of least privilege.
- Multi-Factor Authentication (MFA): Enforce MFA for users with access to create or modify AMIs. This adds an extra layer of security and prevents unauthorized access even if credentials are compromised.
- Monitor IAM Activity: Regularly monitor IAM activity logs to identify any suspicious behavior or unauthorized access attempts related to your AMIs.
By adhering to these security best practices and maintaining a proactive approach to vulnerability management and access control, you can significantly reduce the risk of security breaches within your AWS infrastructure built on AMIs.
Leveraging Advanced AMI Features for Enhanced Functionality: Power Up Your Infrastructure
AMIs offer more than just pre-configured operating systems and applications. This section delves into advanced features that empower you to automate tasks, customize storage configurations, and enhance the security of your data within AMIs.
User Data Scripts: Automating Tasks During Instance Launch
User data scripts are powerful tools that allow you to automate repetitive tasks during the instance launch process. These scripts are executed as the root user on the first boot of an instance and can be used for various purposes:
- Installing Additional Software: Instead of manually installing software on each instance, utilize user data scripts to automate the installation process. This ensures consistency and reduces deployment time.
- Configuring System Settings: Configure system settings like time zones, file permissions, or user accounts through user data scripts. This streamlines configuration management and eliminates manual intervention.
- Running Custom Commands: Execute any commands or scripts needed to prepare your instance for its specific role within your application environment. User data scripts offer flexibility for various customization tasks.
Benefits of Utilizing User Data Scripts:
- Reduced Deployment Time: Automate repetitive tasks and configuration steps, leading to faster deployments.
- Consistency and Repeatability: Ensure consistent configuration across all instances launched from the same AMI.
- Improved Security: Use scripts to automate security hardening tasks, minimizing the risk of human error.
Important Considerations:
- Security Best Practices: Exercise caution when using user data scripts, as they run with root privileges. Ensure scripts are secure and avoid embedding sensitive information directly within them.
- Troubleshooting Challenges: If a script fails during launch, troubleshooting can be more complex compared to manual configuration. Implement logging mechanisms within your scripts to assist with debugging.
Block Device Mappings: Customizing Storage Configurations
AMIs define the root device for instances, typically an EBS volume. However, block device mappings allow you to further customize storage configurations:
- Attaching Additional EBS Volumes: Specify additional EBS volumes to be attached to instances launched from your AMI. This provides additional persistent storage for your applications.
- Customizing EBS Volume Types: Choose between various EBS volume types (e.g., General Purpose SSD, Magnetic) depending on your workload requirements for performance and cost optimization.
- Ephemeral Storage with Instance Store Volumes: Map instance store volumes to your AMI, providing temporary storage that is lost upon instance termination. This can be useful for temporary files or caches.
Benefits of Utilizing Block Device Mappings:
- Scalable Storage: Easily scale your storage capacity by attaching additional EBS volumes as your application needs grow.
- Performance Optimization: Select the appropriate EBS volume type to match the performance requirements of your applications.
- Cost-Effectiveness: Choose between cost-optimized EBS volume types or leverage instance store volumes for temporary data, optimizing your storage spend.
Important Considerations:
- Managing Snapshots: Regularly back up your data on EBS volumes using snapshots to ensure data protection in case of accidental deletion or instance failures.
- Security Implications: Ensure proper encryption of data stored on EBS volumes to protect sensitive information in case of unauthorized access.
Encryption: Protecting Your Data Within AMIs
Security is paramount, and AMIs can be a potential target for attackers seeking access to sensitive data. Encryption safeguards your data at rest within AMIs:
- AMI Encryption with AWS KMS: Utilize AWS Key Management Service (KMS) to encrypt your AMIs with customer-managed keys. This ensures only authorized users can access the decrypted AMI content.
- EBS Volume Encryption: Encrypt EBS volumes attached to your instances to protect data at rest on the storage volumes themselves.
Benefits of Utilizing Encryption:
- Enhanced Data Security: Encryption adds an extra layer of protection for sensitive information stored within AMIs and on EBS volumes.
- Regulatory Compliance: Encryption can help meet compliance requirements for data security in certain industries or regulations.
Important Considerations:
- Key Management: Implement robust key management practices for your encryption keys. This includes secure storage and access controls for these keys.
- Performance Impact: Encryption can introduce a slight overhead during instance launch and data access. However, the security benefits typically outweigh this performance consideration.
By leveraging these advanced AMI features, you can automate tasks, customize your infrastructure’s storage configuration, and enhance the security posture of your data within the AWS cloud.
Troubleshooting Common AMI Issues: Resolving Challenges Efficiently
Even with well-crafted AMIs, you may encounter occasional issues during deployment or instance launch. This section equips you with the knowledge to troubleshoot common AMI problems and maintain a healthy cloud environment.
Common Error Messages and Troubleshooting Steps
AMI Not Found: This error indicates the specified AMI ID doesn’t exist or you lack permission to access it.
- Double-check the AMI ID: Ensure you’re using the correct AMI ID for the instance launch.
- Verify IAM Permissions: Confirm your IAM role or user has the necessary permissions to launch instances from the desired AMI.
Invalid Device Name: This error signifies a mismatch between the device name specified in your launch configuration and the actual device names within your AMI.
- Review Block Device Mappings: Verify that the device names in your launch configuration or user data scripts match the devices defined within your AMI’s block device mappings.
Insufficient Instance Capacity: This error occurs when the chosen instance type is unavailable in the specified Availability Zone.
- Monitor Instance Availability: Use the AWS Management Console or CLI to check the availability of your desired instance type in the chosen Availability Zone. Consider launching in a different zone or selecting a different instance type with available capacity.
Security Group Configuration Issues: This error indicates a problem with the security groups assigned to your instance.
- Review Security Group Rules: Ensure the security groups allow inbound traffic on the required ports for your application to function. Double-check for any accidentally blocked ports.
These are just a few examples, and the specific error message will guide you towards the root cause of the issue. The AWS documentation provides detailed information on various error messages and troubleshooting steps.
Debugging Launch Failures Associated with AMIs
If your instance launch fails specifically due to issues with your AMI, here are some debugging steps:
- Review User Data Script Logs: If you utilize user data scripts, check the cloud-init logs on your instance for any errors during script execution. These logs can provide clues about what went wrong during the initial configuration steps.
- Test the Base AMI: Launch an instance from the base AMI (e.g., Amazon Linux 2) used to build your custom AMI. This helps isolate if the issue lies within the base image itself or the additional software and configuration applied within your custom AMI.
- Utilize AWS Support: If you’re unable to resolve the launch failure independently, consider reaching out to AWS Support for further assistance. They can provide deeper insights and troubleshooting guidance specific to your situation.
Best Practices for Maintaining a Healthy Cloud Environment
- Regular AMI Updates: Patch your AMIs regularly to address known vulnerabilities in the operating system and applications. Consider automation tools to streamline the patching process.
- Monitor Instance Health: Utilize AWS CloudWatch to monitor the health and performance of your instances. This allows you to identify potential issues early on and take corrective actions.
- Test and Validate Changes: Before deploying a new AMI version to production, thoroughly test it in a staging environment. This ensures functionality, compatibility, and adherence to security best practices.
- Maintain Backups: Regularly back up your data to Amazon S3 or EBS snapshots. This ensures you can recover your data in case of accidental deletion or instance failures.
- Review IAM Permissions: Periodically review and update IAM permissions to ensure they are aligned with the principle of least privilege. This minimizes the risk of unauthorized access to your AMIs and resources.
By following these best practices, you can proactively maintain a healthy cloud environment built upon secure and well-functioning AMIs.
Cost Optimization Strategies for AMIs: Keeping Your Cloud Expenses in Check
Managing your cloud infrastructure costs is crucial for maximizing the value you derive from AWS. AMIs play a significant role in this equation, as they define the underlying resources provisioned for your instances. This section explores strategies to optimize your AMI usage and minimize cloud spend.
Identifying Cost-Effective AMIs
- Consider Free Tier Eligible AMIs: AWS offers a free tier with access to certain base AMIs (e.g., Amazon Linux 2). Utilize these free options for non-critical workloads or development environments.
- Evaluate Marketplace AMI Pricing: Explore the pricing models of AMIs in the AWS Marketplace. Some AMIs are offered with free base licenses, while others may have subscription fees. Choose options that align with your budget and workload requirements.
- Analyze Resource Consumption of AMIs: Utilize AWS Cost Explorer to analyze the historical resource consumption of different AMIs used within your environment. This data can help you identify AMIs with a higher resource footprint and potentially explore more cost-efficient alternatives.
Optimizing Instance Sizes Based on Your Needs
- Rightsize Your Instances: Select the most cost-effective instance type that meets the resource requirements (CPU, memory) of your application. Overprovisioned instances lead to unnecessary expense. Utilize tools like Amazon EC2 Instance Advisor to identify potential opportunities for rightsizing your instances.
- Consider Burstable Instances: For workloads with fluctuating resource demands, explore Burstable Instances. These instances provide a baseline level of CPU performance with the ability to burst to higher levels when needed. This flexibility can be cost-effective compared to continuously running on-demand instances.
- Evaluate Reserved Instances (RIs): If you have predictable workloads with consistent resource requirements, consider Reserved Instances. RIs offer significant discounts compared to on-demand pricing when used for a specific term or usage pattern.
Utilizing Spot Instances for Cost-Savings Opportunities
- Spot Instances: Spot Instances are spare compute capacity in the AWS cloud offered at significantly lower prices than on-demand instances. However, their availability and pricing can fluctuate based on supply and demand.
- Identify Suitable Workloads: Spot Instances are well-suited for fault-tolerant workloads that can handle interruptions if the underlying Spot Instance is terminated due to price changes. Batch processing tasks or non-critical background processes are good candidates for Spot Instances.
- Utilizing Spot Fleet: The Spot Fleet service allows you to automatically request a fleet of Spot Instances with configurable settings for instance types, price, and availability zones. This helps you launch cost-optimized instances while mitigating the risk of a single Spot Instance being interrupted.
By implementing these cost optimization strategies, you can make informed decisions when selecting and utilizing AMIs. Optimizing instance sizes and leveraging cost-saving options like Spot Instances allows you to maintain a robust cloud infrastructure while keeping your AWS expenses under control.
Case Studies: Exploring Real-World Applications of AMIS in Different Industries
AMIs offer a versatile tool for building and deploying infrastructure across various industries. This section delves into real-world case studies showcasing how organizations leverage AMIs to achieve specific goals.
Case Study 1: Building a Scalable Web Application Platform with AMIs
Industry: E-commerce
Challenge: A rapidly growing e-commerce company needed a scalable and reliable platform to handle increasing website traffic and user base. Manual server provisioning and configuration were becoming cumbersome and time-consuming.
Solution: The company implemented a custom AMI strategy:
- Base AMI: They utilized a free tier eligible Amazon Linux 2 AMI for the base image.
- Pre-installed Applications: The AMI included pre-installed web server software (e.g., Nginx), a high-performance database (e.g., PostgreSQL), and a caching layer (e.g., Redis).
- Configuration Management: They leveraged Infrastructure as Code (IaC) tools like Terraform to automate configuration management tasks across their instances launched from the AMI.
- Auto Scaling Groups: The company configured auto scaling groups to automatically scale their web server instances up or down based on website traffic, ensuring optimal performance and resource utilization.
Benefits:
- Faster Deployments: Launching new instances from the pre-configured AMI significantly reduced deployment times compared to manual server provisioning.
- Improved Scalability: Auto scaling groups ensured the platform could automatically handle surges in traffic without manual intervention.
- Consistency and Reliability: The use of a custom AMI with IaC tools ensured consistent configuration across all web server instances, enhancing platform reliability.
B. Case Study 2: Facilitating Data Analysis Workflows Using Custom AMIs
Industry: Healthcare Research
Challenge: A research institution needed to streamline the process of setting up data analysis environments for researchers. Manually installing and configuring software tools on individual workstations was inefficient and time-consuming.
Solution: The institution created a custom AMI specifically tailored for data analysis workflows:
- Base AMI: They chose an Amazon Linux 2 AMI with pre-installed scientific computing libraries like NumPy and SciPy.
- Data Science Tools: The AMI included popular data analysis tools such as Jupyter Notebook, R, and various statistical software packages.
- Environment Variables: The AMI pre-configured environment variables to simplify access to commonly used data storage locations.
- User Data Script: A user data script automatically downloaded and installed any additional software specific to a researcher’s project needs upon instance launch.
Benefits:
- Reduced Setup Time: Researchers could launch pre-configured instances with all necessary tools, eliminating lengthy manual installations.
- Standardized Workflows: The custom AMI ensured a consistent data analysis environment for all researchers, facilitating collaboration and reproducibility.
- Improved Efficiency: Researchers could focus on their analysis tasks instead of spending time setting up their workstations.
Case Study 3: Optimizing Disaster Recovery Strategies with AMIs
Industry: Financial Services
Challenge: A financial services company needed a robust disaster recovery (DR) plan to minimize downtime in case of unexpected outages at their primary data center.
Solution: The company leveraged AMIs for their DR strategy:
- Golden AMI: They maintained a “golden image” AMI containing their production environment configuration and applications. This AMI was regularly updated with the latest code and data backups.
- Regional Deployment: The company deployed their production environment in one region and created an identical AMI-based environment in a separate region for disaster recovery purposes.
- Automated Failover: They implemented automated failover mechanisms to seamlessly switch traffic to the DR environment if an outage occurred in the primary region.
- Testing and Validation: The company conducted regular DR drills to ensure the functionality and effectiveness of their AMI-based failover process.
Benefits:
- Faster Recovery Time: Utilizing pre-configured AMIs in the DR environment enabled rapid restoration of critical services in case of a disaster, minimizing downtime.
- Reduced Cost: By leveraging AMIs, the company avoided the need to provision and maintain duplicate infrastructure in the DR region, optimizing disaster recovery costs.
- Improved Business Continuity: The AMI-based DR strategy ensured the company could maintain business continuity even in the face of unexpected outages.
These case studies showcase the versatility of AMIs in addressing various infrastructure challenges across diverse industries. By leveraging custom AMIs and automation tools, organizations can achieve faster deployments, enhance infrastructure scalability, and optimize their cloud environments for cost-effectiveness and operational efficiency.
The Future of AMIs: Exploring Evolving Trends and Advancements
AMIs, as the foundation for building infrastructure in the cloud, are constantly evolving to keep pace with technological advancements. This section explores emerging trends that will likely shape the future of AMIs and how they are managed.
Integration with Containerization Technologies (e.g., Docker)
- Containerized Applications within AMIs: The popularity of containerization technologies like Docker presents an opportunity to package applications within AMIs as container images. This approach offers several benefits:
- Portability and Isolation: Containerized applications are portable across different environments and provide isolation from the underlying host system, enhancing consistency and security.
- Faster Deployments: Container images are typically smaller than traditional application packages, leading to faster download times during instance launches.
- Microservices Architecture: AMIs can be designed to launch multiple containerized microservices, facilitating the deployment of complex applications with modular components.
- Challenges and Considerations:
- Management Complexity: Managing containerized applications within AMIs introduces additional complexity compared to traditional package-based deployments.
- Security Implications: Container security best practices need to be integrated into the AMI creation process to ensure the overall security posture of the instance.
Leveraging Machine Learning for Automated AMI Management
- Automating AMI Builds and Updates: Machine learning (ML) can be used to automate tasks associated with building and updating AMIs. This includes:
- Predictive Scaling: ML algorithms can analyze historical data to predict resource needs and automatically update AMIs with the appropriate instance types, optimizing resource utilization.
- Automated Patching: ML can identify security vulnerabilities and automate the patching process within AMIs, ensuring timely security updates and reducing the risk of exploitation.
- Anomaly Detection: ML models can monitor AMI builds and deployments for anomalies or potential issues, enabling proactive troubleshooting and preventing disruptions.
- Benefits and Challenges:
- Reduced Operational Overhead: Automation through ML frees up IT staff from repetitive tasks, allowing them to focus on more strategic initiatives.
- Improved Efficiency and Consistency: ML-driven automation can streamline AMI management, resulting in faster deployments and a more consistent infrastructure.
- Data Requirements and Model Training: Effective utilization of ML requires access to relevant data sets and ongoing training of the models to maintain accuracy and effectiveness.
The Rise of Serverless Computing: Impact on AMIs
- Serverless Paradigm: Serverless computing is a cloud computing model where the cloud provider manages the servers and infrastructure, allowing users to focus on developing and deploying code.
- Potential Impact on AMIs: The rise of serverless computing might lead to a decreased reliance on traditional AMIs for specific use cases. However, AMIs are likely to remain relevant for:
- State Management and Long-Running Processes: Serverless functions are stateless and short-lived. AMIs can still be used for applications requiring persistent storage or long-running background processes.
- Hybrid and Multi-Cloud Environments: Organizations with hybrid or multi-cloud deployments might continue to leverage AMIs for consistent infrastructure management across different environments.
- The Future Landscape: A hybrid approach is likely, where AMIs and serverless technologies coexist and complement each other depending on the specific needs of the application.
By staying informed about these evolving trends, businesses can leverage the future of AMIs to build more efficient, scalable, and secure cloud infrastructure. Integration with containerization technologies, automation through machine learning, and understanding the role of AMIs in the context of serverless computing will be crucial for optimizing cloud deployments in the years to come.
Conclusion: AMIs – The Cornerstone of Your AWS Infrastructure
This comprehensive guide has explored AMIs (Amazon Machine Images), the fundamental building blocks for launching instances in your AWS cloud environment. We’ve delved into the core concepts, best practices for management and security, explored advanced features for enhanced functionality, and even examined real-world applications across diverse industries.
Recap of Key Concepts and Benefits
- AMIs Defined: Pre-configured software bundles containing an operating system, applications, and configurations, acting as the blueprint for launching instances in AWS.
- Benefits of Utilizing AMIs:
- Faster Deployments: Launch pre-configured instances, eliminating time-consuming manual server setup.
- Improved Consistency: Ensure consistent configurations across your infrastructure for enhanced reliability.
- Scalability and Flexibility: Easily scale your infrastructure up or down based on your needs.
- Cost Optimization: Leverage cost-effective AMIs and instance types for optimal resource utilization.
- Security Enhancements: Implement security best practices within AMIs to protect your cloud environment.
Call to Action: Start Building and Deploying with AMIs Today!
AMIs empower you to build a robust, secure, and scalable cloud foundation on AWS. By understanding the concepts we’ve covered and implementing the best practices outlined, you can unlock the full potential of AMIs for your cloud deployments.
- Start Experimenting: Explore the AWS Management Console or AWS CLI to create and launch basic AMIs.
- Automate Workflows: Leverage tools like Infrastructure as Code (IaC) to automate AMI creation and deployment processes.
- Explore Advanced Features: Utilize user data scripts, block device mappings, and encryption to customize your AMIs for specific needs.
- Stay Informed: Keep yourself updated on the latest trends in AMI management, such as containerization integration and machine learning automation.
By embracing AMIs and their capabilities, you can streamline your cloud deployments, optimize your infrastructure costs, and empower your organization to thrive in the ever-evolving cloud landscape. Leverage the knowledge gained from this guide and embark on your journey of building a powerful and efficient cloud environment with AMIs as the cornerstone.
Frequently Asked Questions: Demystifying AMIs
This section addresses some of the most common questions regarding AMIs to solidify your understanding of their role within your AWS cloud environment.
What are the differences between AMIS and Snapshots?
- AMIs (Amazon Machine Images): Blueprints for launching EC2 instances. They contain the entire configuration of an instance, including the operating system, applications, and settings. AMIs are used to create new instances with identical configurations.
- Snapshots: Backups of EBS (Elastic Block Store) volumes, which store the data persisting on your instances. Snapshots capture the state of an EBS volume at a specific point in time. You can use snapshots to restore data on a failing volume, create new volumes from existing ones, or migrate data between Availability Zones.
In simpler terms:
- AMIs are like recipes that define the ingredients (software, configuration) needed to build a new server (instance).
- Snapshots are like backups of your kitchen ingredients (data on EBS volumes), allowing you to restore them or create copies for other dishes (instances).
How long can I store an AMI?
You can store an AMI in your AWS account indefinitely, as long as you continue to pay for the storage associated with it. There are no automatic expiration policies for AMIs. However, it’s recommended to deregister unused AMIs to avoid unnecessary storage charges.
Can I modify a running instance and create a new AMI from it?
Yes, you can modify a running instance by installing additional software, changing configurations, or updating data. Once the modifications are complete, you can create a new AMI from the modified instance. This allows you to capture the current state of the instance, including your customizations, for future deployments.
Here are two methods for creating an AMI from a modified instance:
- AWS Management Console: Navigate to the EC2 service and right-click on the desired instance. Select “Create Image” from the context menu and follow the on-screen instructions.
- AWS CLI: Utilize the ec2 create-image command to create an AMI from the instance ID.
What are the security implications of sharing AMIs?
Sharing AMIs can be beneficial for collaboration within your organization. However, it’s crucial to understand the security implications:
- Permissions: Grant access to AMIs only to users or groups who require them for deployments. Avoid sharing AMIs publicly unless they contain no sensitive information.
- Vulnerabilities: An AMI with security vulnerabilities can be replicated across all instances launched from it. Ensure your AMIs are built with security best practices in mind and regularly patch them to address known vulnerabilities.
- Data Exposure: If your AMI contains sensitive data within the operating system or applications, sharing it exposes that data to anyone with access to the AMI. Be mindful of the data included within your AMIs.
Best Practices for Secure AMI Sharing:
- Utilize private AMIs for internal use within your organization.
- Implement granular IAM policies to control access to AMIs.
- Regularly scan AMIs for vulnerabilities and patch them promptly.
- Avoid including sensitive data within AMIs.
How can I migrate my existing on-premises infrastructure to AWS using AMIs?
There are several approaches to migrate your on-premises infrastructure to AWS using AMIs:
- Manual AMI Creation: Create a custom AMI on AWS that replicates the configuration of your on-premises servers. This can be time-consuming for complex environments.
- AWS Migration Hub: AWS Migration Hub offers tools and services to simplify the migration process. You can use tools like AWS Server Migration Service (SMS) to migrate on-premises servers to EC2 instances and create AMIs during the migration process.
- Third-Party Migration Tools: Several third-party tools specialize in migrating on-premises environments to the cloud. These tools can automate tasks like creating AMIs from your existing servers.
Choosing the Right Migration Approach:
The optimal migration approach depends on the complexity of your on-premises environment, your technical expertise, and budget constraints. Consider utilizing AWS resources and documentation to guide your migration journey.
Popular Courses