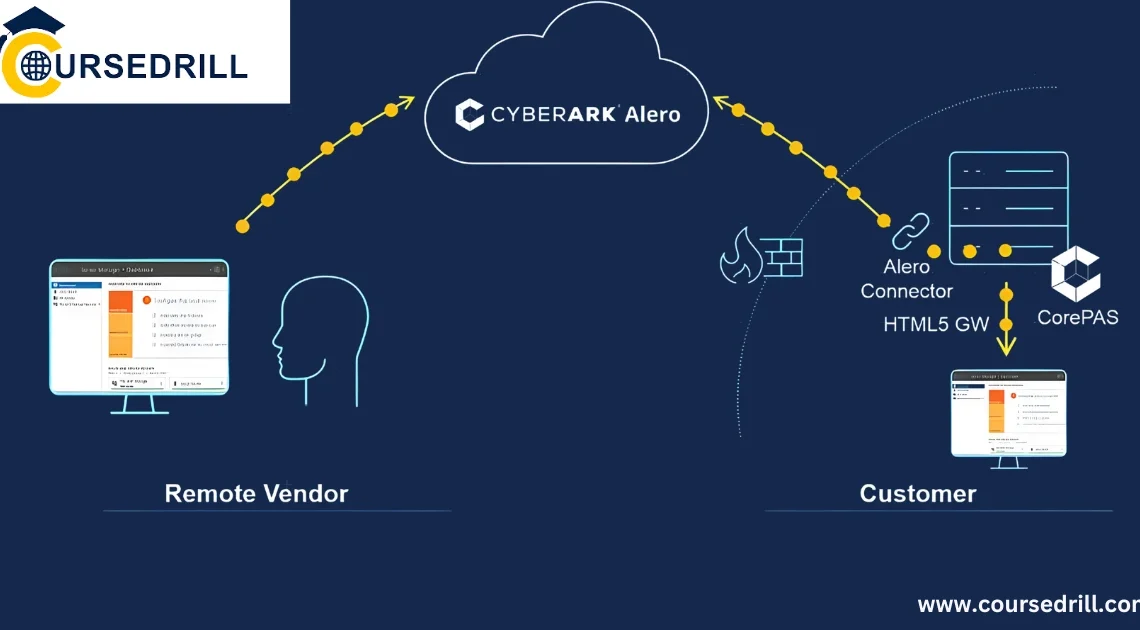
A Deep Dive Into the Core Components of CyberArk Architecture Introduction The Critical Need for Privileged Access Management (PAM) Start with a real-world scenario highlighting the risks of unsecured privileged accounts (e.g., data breaches, ransomware attacks). Define Privileged Access Management (PAM) and its role in […]