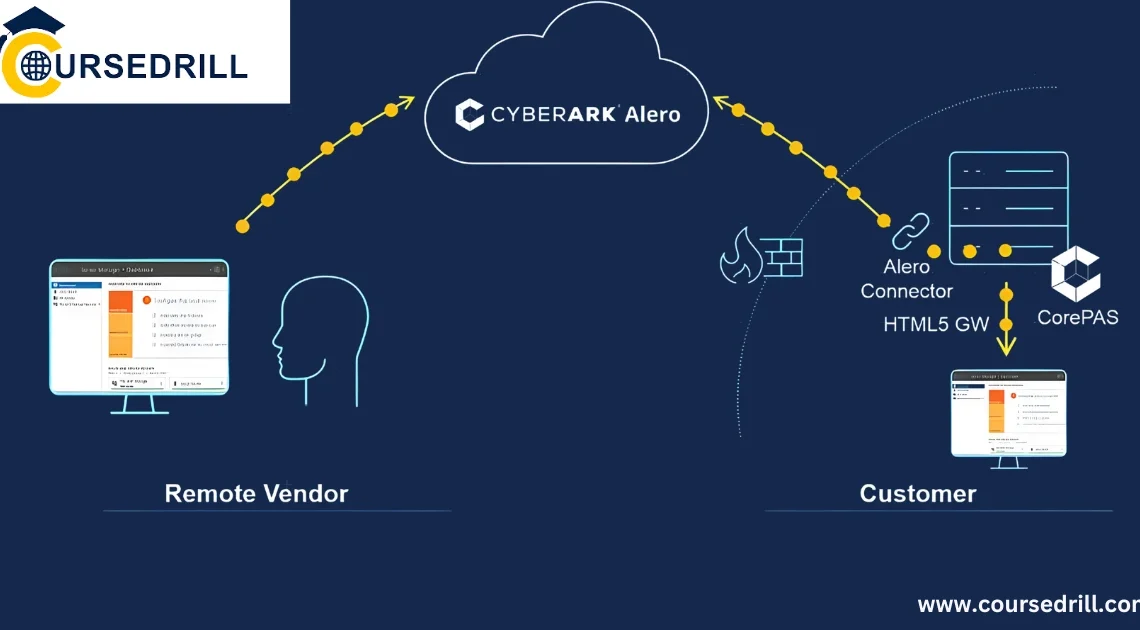
CyberArk Components Explained: From Vault to Session Management Introduction: The Fortress and its Tools Understanding the Privileged Access Management (PAM) landscape: Imagine a vast castle, brimming with sensitive information and critical systems. Protecting this treasure trove are multiple layers of security, but a hidden vulnerability […]