- Posted on
- admin
- No Comments
A Deep Dive Into the Core Components of CyberArk Architecture
Introduction
The Critical Need for Privileged Access Management (PAM)
- Start with a real-world scenario highlighting the risks of unsecured privileged accounts (e.g., data breaches, ransomware attacks).
- Define Privileged Access Management (PAM) and its role in protecting sensitive data and systems.
- Briefly discuss the limitations of traditional methods for managing privileged accounts (e.g., manual controls, hardcoded passwords).
Unveiling the Power of CyberArk: A Solution Overview
- Introduce CyberArk as a leading PAM solution and its core value proposition.
- Briefly touch upon the different deployment options (on-premises, cloud, hybrid).
- Provide a high-level overview of the key benefits of using CyberArk (e.g., improved security, reduced risk, compliance, efficiency gains).
Core Components: Building Blocks of Security
The CyberArk Digital Vault: Securely Housing Privileged Credentials
- Elaborate on the different vault types (e.g., Self-Hosted, Cloud-Based, Hybrid) and their advantages.
- Explain the encryption methods used to secure credentials within the vault.
- Describe the access control mechanisms employed to restrict unauthorized access.
- Discuss the importance of vault auditing and logging for monitoring and compliance.
Privileged Account Manager (PAM): Centralized Control and Governance
- Explain how PAM helps manage privileged accounts across diverse systems and platforms.
- Discuss the implementation of the Least Privilege Principle and Role-Based Access Control (RBAC).
- Describe the functionalities for password rotation and automated management of privileged accounts.
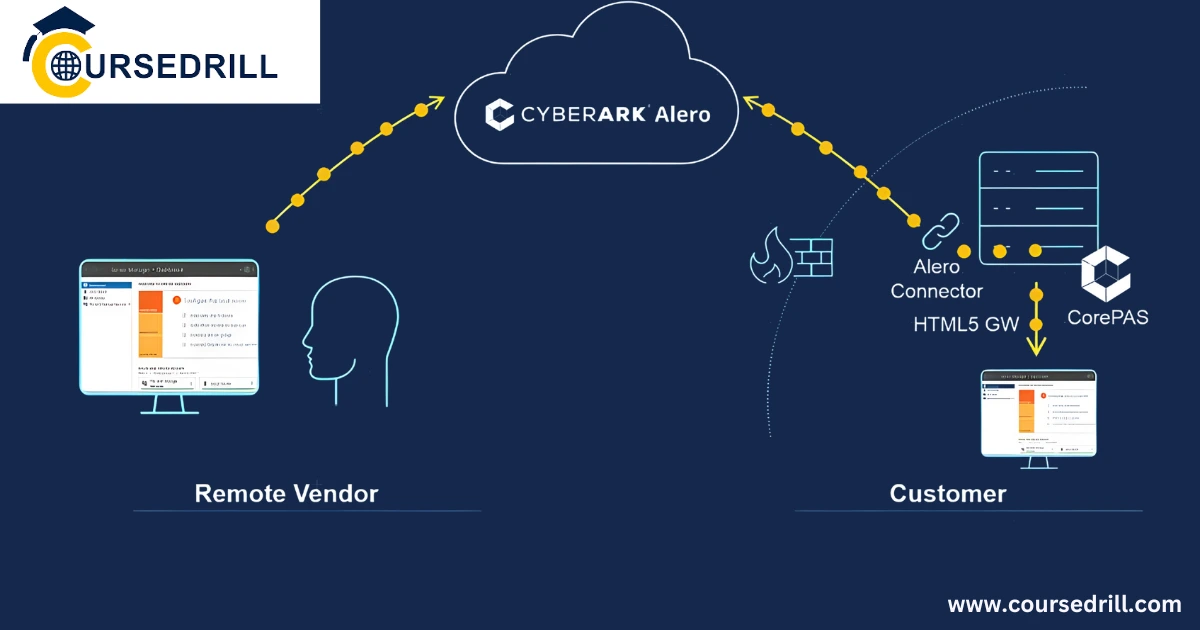
Privileged Session Manager (PSM): Secure Remote Access and Monitoring
- Explain how PSM enables secure remote access to privileged sessions.
- Describe the session recording and activity monitoring features for enhanced visibility and control.
- Discuss Just-in-Time (JIT) Privileging and its role in minimizing exposure and attack surfaces.
- Briefly mention Application Access Control and session termination capabilities.
Advanced Modules: Extending the Security Net
On-Demand Privileges Manager (OPM): Empowering Users with Least Privilege
- Explain how OPM provides secure elevation of privileges for Unix environments.
- Discuss its seamless integration with existing PAM solutions and how it streamlines workflows.
- Highlight the benefits of OPM in reducing risk and improving user experience.
Endpoint Privilege Management (EPM): Securing Local Administrator Accounts
- Explain how EPM helps centralize the management and control of local administrator accounts.
- Discuss application control and whitelisting functionalities for increased security.
- Describe how EPM reduces attack surfaces and mitigates lateral movement within the network.
Password Vault: Securely Storing and Managing Sensitive Credentials
- Explain how Password Vault goes beyond privileged accounts to manage non-privileged credentials.
- Discuss advanced security features like multi-factor authentication and encryption.
- Highlight the streamlined workflow and user experience benefits of Password Vault.
Want to become high-paying cybersecurity professional? Then check out our expert's designed and deliverable CyberArk training program. Get advice from experts.
Deployment Options: Choosing the Right Fit for Your CyberArk Architecture
When deploying CyberArk, selecting the right option depends on your specific needs, security posture, and infrastructure. Here’s a deeper dive into the three primary deployment models:
On-Premises Deployment: Full Control and Customization
Pros:
Offers complete control over your security infrastructure.
Allows for customization to meet specific organizational requirements.
No reliance on third-party cloud providers for data storage and processing.
Ideal for organizations with strict data privacy regulations or security concerns about cloud environments.
Cons:
Requires significant upfront investment in hardware, software, and IT expertise for maintenance.
Less scalable than cloud options, making it challenging to adapt to changing needs.
May be susceptible to physical security breaches if not adequately protected.
Cloud Deployment: Scalability and Agility
- Pros:
- Offers rapid deployment and scalability, allowing for quick adaptation to changing needs.
- Reduces the burden of managing hardware and software infrastructure.
- Lower upfront costs compared to on-premises deployments.
- Many cloud providers offer robust security features and compliance certifications.
- Cons:
- Relies on a third-party provider, potentially introducing additional security concerns.
- Less control over data location and access compared to on-premises options.
- Vendor lock-in can be an issue, making it difficult to switch providers later.
Hybrid Deployment: Combining On-Premises and Cloud Advantages
Pros:
Offers a flexible and customizable approach, allowing you to leverage the benefits of both on-premises and cloud deployments.
Sensitive data can be stored on-premises for enhanced security, while less critical data can be placed in the cloud for scalability.
Provides a disaster recovery solution by replicating data between on-premises and cloud environments.
Cons:
Complexity increases, requiring careful management and orchestration across both environments.
Security needs to be addressed in both on-premises and cloud components.
Requires technical expertise to manage and secure the hybrid environment effectively.
Choosing the Right Fit:
The ideal deployment option depends on various factors, including:
- Security requirements: Organizations with strict data privacy regulations may favor on-premises deployments, while others may find cloud security sufficient.
- Scalability needs: If your organization anticipates rapid growth, cloud deployment’s scalability may be crucial.
- IT resources and expertise: On-premises deployments require significant internal IT expertise for management, while cloud options offer managed services.
- Budget: On-premises deployments have higher upfront costs, while cloud options typically have lower upfront costs but may incur ongoing subscription fees.
Additional Considerations:
- Data residency: If your organization has strict data residency requirements, consider cloud providers that offer regional data storage options.
- Compliance requirements: Ensure your chosen deployment option meets any relevant industry regulations or security compliance standards.
- Integration with existing infrastructure: Evaluate how easily the chosen deployment option integrates with your existing IT infrastructure.
Integration and Automation: Streamlining Security Processes with CyberArk
In today’s complex IT landscape, manual security processes can be cumbersome, error-prone, and inefficient. CyberArk’s integration and automation capabilities offer a powerful solution, streamlining your security workflows and enhancing overall effectiveness. Let’s delve deeper into how each element empowers you:
Integrating CyberArk with Existing IT Infrastructure:
Seamless connectivity: CyberArk integrates with a wide range of IT systems and platforms, including Active Directory, LDAP, Unix/Linux systems, cloud platforms like AWS and Azure, and security information and event management (SIEM) solutions.
Reduced complexity: Eliminates manual data entry and reconciliation, minimizing errors and streamlining user provisioning and access management.
Enhanced visibility and control: Provides a central console for managing privileged access across diverse environments, offering a consolidated view and simplified administration.
Improved security posture: Streamlined integration reduces security gaps and vulnerabilities associated with manual processes, strengthening your overall security posture.
Here are some specific integration examples:
Active Directory: Automatically synchronize user accounts and privileges between CyberArk and Active Directory, ensuring consistency and reducing manual effort.
Unix/Linux systems: Leverage CyberArk to manage SSH keys and sudo privileges, enforcing least privilege principles and enhancing control over privileged access.
Cloud platforms: Integrate with cloud providers like AWS and Azure to securely manage privileged access to cloud resources, ensuring compliance and preventing unauthorized access.
Automating Security Tasks and Workflows:
Scriptable actions: Automate repetitive tasks like password resets, account creation/deletion, privilege elevation requests, and access approvals, saving time and resources.
Policy-based automation: Define automated actions based on pre-defined policies, ensuring consistent enforcement of security rules and eliminating human error.
Workflow orchestration: Combine multiple automated actions into complex workflows, streamlining processes like incident response and remediation.
Improved efficiency: Reduces manual intervention, freeing up security teams to focus on strategic initiatives and investigations.
Here are some specific automation examples:
Automated password resets: Automatically reset expired passwords for privileged accounts, ensuring timely access and reducing password fatigue.
Just-in-Time (JIT) provisioning: Grant temporary privileged access only when needed, minimizing exposure and reducing attack surfaces.
Automated access approvals: Automate the approval process for privileged access requests based on pre-defined criteria, expediting approvals and improving efficiency.
Reducing Manual Intervention and Improving Efficiency:
Reduced administrative burden: Automation frees up security personnel from repetitive tasks, allowing them to focus on more strategic initiatives and investigations.
Improved accuracy and consistency: Automation eliminates manual errors and ensures consistent enforcement of security policies across the organization.
Faster incident response: Automated workflows facilitate rapid response to security incidents, minimizing damage and downtime.
Enhanced compliance: Streamlined processes and automated controls simplify compliance with industry regulations and security standards.
By leveraging CyberArk’s integration and automation capabilities, you can achieve:
Reduced security risks: By minimizing manual intervention and enforcing consistent policies, you significantly reduce the risk of human error and unauthorized access.
Improved operational efficiency: Streamlined workflows and automated tasks free up valuable resources, allowing your security team to focus on higher-level priorities.
Enhanced compliance: Automated controls and consistent enforcement of policies simplify compliance with industry regulations and standards.
Remember, this is just a starting point. You can further enhance your content by:
Providing specific examples and case studies of successful integration and automation implementations.
Highlighting the return on investment (ROI) potential of these capabilities.
Addressing potential challenges and concerns related to integration and automation, such as security considerations and change management.
Security and Compliance: Fortifying Your Defenses with CyberArk
In today’s digital landscape, securing privileged access is paramount. CyberArk equips you with robust security mechanisms and compliance tools to build a fortified wall against cyber threats and ensure adherence to regulations. Let’s explore these key elements:
Multi-Factor Authentication (MFA) and Secure Access:
- Multi-layered defense: Implement robust MFA to add an extra layer of protection beyond passwords. This could include fingerprint scanners, security tokens, or one-time passcodes, significantly reducing the risk of unauthorized access.
- Adaptive authentication: Leverage advanced features like risk-based authentication, which dynamically adjusts security measures based on user behavior and access attempts, further strengthening security posture.
- Granular access control: Define granular access permissions for each user and application, ensuring they only have the minimum access required, minimizing potential attack surfaces.
- Secure remote access: Securely access privileged accounts remotely through CyberArk’s Privileged Session Manager (PSM), with features like session recording, access recording, and application control providing enhanced visibility and control.
Role-Based Access Control (RBAC) and Permission Granularity:
- Least privilege principle: Implement RBAC to assign roles and permissions based on the principle of least privilege, granting users only the access necessary for their job functions, minimizing potential damage in case of compromise.
- Dynamic access control: Utilize dynamic RBAC, where access permissions automatically adjust based on user context, location, time, or application, further enhancing security and compliance.
- Fine-grained control: Define granular permissions within roles, allowing you to precisely control what users can do within their assigned access level, minimizing the risk of misuse.
- Separation of duties: Enforce separation of duties by assigning critical tasks to different individuals, preventing any single user from having excessive privileges.
Compliance with Industry Standards and Regulations:
- Pre-built compliance reports: Streamline compliance efforts with pre-built reports that map to various industry standards and regulations, including PCI DSS, HIPAA, GDPR, and SOX.
- Auditing and logging: Maintain comprehensive audit logs and reports of all privileged access activity, ensuring visibility into user actions and simplifying compliance audits.
- Continuous monitoring: Leverage CyberArk’s continuous monitoring capabilities to identify and address potential security risks proactively, staying ahead of compliance requirements.
- Demonstrable controls: Provide concrete evidence of security controls and access management practices, simplifying compliance demonstrations to regulatory bodies.
By implementing these security and compliance measures within CyberArk, you can achieve:
- Reduced risk of breaches: Multi-layered authentication, granular access control, and least privilege principles significantly reduce the risk of unauthorized access and subsequent breaches.
- Enhanced compliance posture: Streamlined reporting, comprehensive audit logs, and continuous monitoring simplify compliance efforts and ensure adherence to regulations.
- Improved security visibility: Gain centralized visibility into privileged access activity across your entire IT infrastructure, enabling proactive threat detection and response.
- Peace of mind: Knowing your privileged access is secure and compliant allows you to focus on your core business operations with confidence.
Remember:
- Tailor your security and compliance approach to your specific industry regulations and organizational needs.
- Regularly review and update your security policies and access controls to adapt to evolving threats and compliance requirements.
- Seek expert guidance to ensure optimal implementation and utilization of CyberArk’s security and compliance features.
By taking a proactive approach to security and compliance with CyberArk, you can build a robust defense against cyber threats and operate with confidence in today’s ever-changing digital landscape.
Administration and Management: Maintaining Control with CyberArk
CyberArk empowers you to secure privileged access, but effective administration and management are crucial to maintain that control and ensure optimal security posture. Let’s delve into the key pillars of this aspect:
User Management and Role Definitions:
- Centralized user management: Simplify user provisioning, deletion, and access updates through a centralized console, eliminating the need for manual configuration across disparate systems.
- Granular role definitions: Define detailed roles with specific permissions and access levels, aligning them with users’ job functions and the principle of least privilege.
- Dynamic role assignment: Leverage dynamic roles that automatically adjust permissions based on user context, location, time, or application, enhancing security and adapting to changing needs.
- Separation of duties: Implement segregation of duties by assigning critical tasks to different individuals, preventing any single user from having excessive privileges.
- User lifecycle management: Automate user lifecycle processes like onboarding, termination, and access reviews, streamlining administration and ensuring consistent security practices.
Auditing and Reporting for Visibility and Insight:
- Comprehensive audit logs: Capture detailed logs of all privileged access activity, including user actions, access requests, and session recordings.
- Customizable reports: Generate reports tailored to your specific needs, providing insights into user behavior, access patterns, and potential security risks.
- Real-time monitoring: Leverage real-time dashboards and alerts to proactively identify suspicious activity and potential breaches.
- Compliance reporting: Utilize pre-built compliance reports that map to various industry standards and regulations, simplifying compliance audits and demonstrations.
- Forensics and investigations: Utilize audit logs and session recordings for forensic analysis and investigation of security incidents, enabling faster resolution and mitigation.
Disaster Recovery and Business Continuity Planning:
- High availability: Deploy CyberArk in a high-availability configuration to ensure continuous access to privileged credentials even in case of hardware or software failures.
- Data backup and recovery: Implement robust data backup and recovery procedures to ensure the quick restoration of critical information in case of disasters.
- Disaster recovery testing: Regularly test your disaster recovery plan to ensure its effectiveness and identify any potential gaps or vulnerabilities.
- Business continuity planning: Integrate CyberArk with your broader business continuity plan to ensure minimal business disruption in case of unforeseen events.
- Incident response planning: Develop an incident response plan outlining steps to take in case of a security breach, including user account lockouts, access revocation, and communication protocols.
By effectively managing CyberArk administration, you can achieve:
- Enhanced security posture: Granular user management, access control, and auditing provide comprehensive oversight and control over privileged access.
- Streamlined operations: Centralized management and automation reduce administrative overhead and improve operational efficiency.
- Improved compliance: Streamlined reporting and audit logs simplify compliance demonstrations and ongoing monitoring.
- Faster incident response: Proactive monitoring and investigation capabilities enable quicker response to security threats, minimizing potential damage and downtime.
- Enhanced business resilience: Disaster recovery and business continuity planning ensure minimal disruption and continued operations even in unforeseen circumstances.
Remember:
- Tailor your administration and management practices to your specific organizational needs and security requirements.
- Regularly review and update your user roles, access controls, and auditing policies to adapt to evolving threats and compliance changes.
- Train your administrators on proper CyberArk usage and best practices to ensure they understand their critical role in maintaining security.
- Conduct regular security audits and penetration testing to identify and address any potential vulnerabilities within your CyberArk environment.
By taking a comprehensive approach to administration and management, CyberArk can be a powerful tool in your organization’s security arsenal, protecting your privileged access and ensuring business continuity in the face of ever-present threats.
Futureproofing Your Security: Emerging Trends and Innovations in CyberArk Architecture
The digital landscape is constantly evolving, and so are the threats targeting your privileged access. To stay ahead of the curve, it’s crucial to embrace emerging trends and innovations that can futureproof your security posture. Let’s explore how CyberArk is incorporating these advancements:
Artificial Intelligence and Machine Learning in PAM (Privileged Access Management):
- Enhanced anomaly detection: AI and machine learning algorithms can analyze user behavior, access patterns, and system activity to identify anomalies and suspicious activities in real-time, enabling proactive threat detection and prevention.
- Automated threat response: These intelligent systems can automatically trigger pre-defined actions in response to identified threats, such as locking accounts, suspending sessions, or notifying security personnel, minimizing damage and response times.
- Predictive analytics: AI can analyze historical data and identify trends to predict potential security risks and vulnerabilities before they occur, allowing for proactive mitigation strategies.
- Adaptive security: Machine learning algorithms can dynamically adjust security policies and access controls based on real-time threat intelligence and user behavior, ensuring the most appropriate level of security for each situation.
Cloud-Native and Hybrid Security Solutions:
- Scalability and agility: Cloud-native deployments offer rapid scalability and on-demand resources, allowing you to easily adapt to changing business needs and security threats.
- Reduced infrastructure burden: Eliminate the need to manage and maintain on-premises hardware, reducing IT overhead and complexity.
- Improved collaboration: Cloud-based solutions facilitate collaboration between security teams across different locations, enhancing overall threat detection and response capabilities.
- Hybrid flexibility: Hybrid deployments combine the benefits of both on-premises and cloud environments, allowing you to tailor your security solution to your specific needs and data residency requirements.
Zero Trust Architecture and Privileged Access:
- Least privilege enforcement: Zero trust principles ensure that every user and device is granted the minimum access required to perform their tasks, regardless of their location or identity.
- Continuous verification: Users and devices are continuously authenticated and authorized before granting access, minimizing the risk of unauthorized access even if credentials are compromised.
- Dynamic access control: Access privileges are dynamically adjusted based on user context, location, time, and application, further minimizing attack surfaces and potential damage.
- Micro-segmentation: Network segmentation is implemented at a granular level, minimizing the impact of a breach and preventing lateral movement within your network.
CyberArk is actively incorporating these innovations into its platform, offering:
- AI-powered threat detection and anomaly analysis.
- Cloud-native deployment options for scalability and agility.
- Integration with Zero Trust frameworks for enhanced security.
By embracing these future-proof solutions, you can achieve:
- Improved protection against evolving threats: AI-powered detection and proactive mitigation strategies ensure your security posture remains resilient against new and emerging threats.
- Enhanced operational efficiency: Cloud-native solutions reduce infrastructure burden and enable flexible scaling, adapting to your changing needs.
- Zero Trust security posture: Minimize attack surfaces and grant least privilege access, significantly reducing the risk of breaches and their impact.
Remember:
- Regularly evaluate your security needs and threat landscape to identify emerging trends and potential vulnerabilities.
- Stay informed about CyberArk’s latest innovations and updates to ensure you leverage the most advanced security features.
- Conduct proof-of-concept deployments and pilot programs to test new technologies and assess their suitability for your organization.
- Seek expert guidance to effectively integrate new solutions and ensure they complement your existing security architecture.
By actively embracing emerging trends and innovations in CyberArk, you can futureproof your security posture, proactively address evolving threats, and ensure the continued protection of your privileged access in the ever-changing digital landscape.
Case Studies: Seeing CyberArk in Action
Real-World Examples of Successful Implementations:
Go beyond theoretical benefits by showcasing real-world success stories. Choose diverse case studies that highlight:
Industry: Showcase implementations across various industries (e.g., finance, healthcare, retail) to demonstrate broad applicability.
Organization size: Include examples from large enterprises and smaller businesses to appeal to a wider audience.
Specific challenges addressed: Focus on case studies where CyberArk addressed specific pain points like:
Data breaches: Highlight how CyberArk prevented or mitigated data breaches.
Compliance challenges: Showcase how CyberArk helped achieve compliance with specific regulations.
Operational inefficiencies: Demonstrate how CyberArk streamlined manual processes and improved efficiency.
Quantifying the Benefits: ROI and Security Improvements:
Don’t just tell, show! Use quantifiable data to paint a clear picture of the value proposition:
- Reduced costs: Quantify cost savings achieved through reduced breaches, compliance fines, and operational overhead.
- Increased productivity: Show how time saved from manual tasks translates to increased productivity and ROI.
- Improved security posture: Use metrics like reduced access attempts, successful privilege escalations prevented, or faster incident response times.
Here’s an example structure for each case study:
Company Name & Industry: Briefly introduce the company and its industry.
Challenge: Describe the specific security challenges the company faced before implementing CyberArk.
Solution: Explain how CyberArk was implemented and which features were used to address the challenges.
Results: Quantify the benefits achieved, including cost savings, productivity gains, and security improvements.
Quote: Include a quote from a company representative expressing their satisfaction with CyberArk.
Additional Tips:
- Use visuals like screenshots and logos to enhance engagement.
- Provide links to the full case studies for readers who want to learn more.
- Tailor the case studies to your target audience, highlighting their specific pain points and concerns.
By presenting concrete examples and quantifiable data, you can paint a compelling picture of how CyberArk can benefit organizations in the real world. This will resonate with potential users and build trust in your content
Conclusion: The Power of a Secure Foundation – Securing Your Privileged Access with CyberArk
Throughout this exploration of CyberArk architecture, we’ve delved into its core components, advanced modules, deployment options, and administrative practices. We’ve seen how it integrates with existing IT infrastructure, automates workflows, and bolsters security and compliance. Now, let’s solidify our understanding by summarizing the key benefits, addressing potential concerns, and issuing a call to action for securing your privileged access.
Key Benefits of CyberArk Architecture:
- Enhanced security: Multi-layered authentication, granular access control, and least privilege principles significantly reduce the risk of unauthorized access and breaches.
- Improved efficiency: Streamlined administration, automated tasks, and centralized management significantly reduce manual effort and improve operational efficiency.
- Simplified compliance: Pre-built reports, comprehensive audit logs, and continuous monitoring make compliance demonstrations and ongoing adherence easier.
- Scalability and agility: Cloud-native and hybrid deployment options offer flexibility and adaptability to your evolving needs.
- Future-proofed security: AI-powered threat detection, Zero Trust integration, and continuous innovation ensure your defenses stay ahead of evolving threats.
Addressing Challenges and Considerations:
- Cost: While upfront costs might seem high, consider the long-term savings from reduced breaches, compliance fines, and operational inefficiencies. Evaluate the ROI potential based on your specific needs.
- Complexity: Implementing and managing CyberArk effectively requires expertise. Consider training your team or seeking expert guidance to ensure optimal utilization.
- Integration: Ensure your existing IT infrastructure can integrate seamlessly with CyberArk. Evaluate compatibility and potential integration challenges beforehand.
A Call to Action: Secure Your Privileged Access, Today!
In today’s digital landscape, privileged access security is no longer optional, it’s imperative. CyberArk empowers you to build a robust defense, protecting your most critical assets and ensuring business continuity. Take the first step towards a more secure future:
- Schedule a demo: Experience CyberArk firsthand and see how it can address your specific needs.
- Download a free trial: Evaluate its features and functionality in your own IT environment.
- Explore resources: Visit the CyberArk website for white papers, case studies, and expert insights.
Remember, securing your privileged access is an ongoing journey, not a one-time destination. By leveraging CyberArk’s comprehensive architecture and staying informed about emerging threats and innovations, you can build a resilient security posture and protect your organization from the ever-evolving landscape of cyber threats.
Start your journey towards a more secure future, today!
Frequently Asked Questions (FAQs) about CyberArk
What are the differences between the various CyberArk components?
CyberArk Digital Vault: Securely stores and manages privileged credentials, offering different vault types (on-premises, cloud, hybrid) for flexibility.
Privileged Account Manager (PAM): Centrally manages privileged accounts across diverse systems and platforms, enforcing least privilege and automating tasks.
Privileged Session Manager (PSM): Enables secure remote access to privileged sessions with features like session recording and activity monitoring.
Advanced Modules: Extend the security net with additional functionalities:
On-Demand Privileges Manager (OPM): Provides secure elevation of privileges for Unix environments.
Endpoint Privilege Management (EPM): Centrally manages and controls local administrator accounts.
Password Vault: Securely stores and manages non-privileged credentials.
How does CyberArk integrate with my existing IT infrastructure?
CyberArk integrates with a wide range of IT systems and platforms through APIs, connectors, and pre-built integrations. It can also connect to security information and event management (SIEM) solutions for centralized visibility.
What are the security benefits of using CyberArk?
- Multi-factor authentication and granular access control: Reduce unauthorized access and data breaches.
- Least privilege enforcement: Minimizes potential damage in case of compromise.
- Auditing and logging: Provides comprehensive insights into user activity and potential security risks.
- Compliance with industry standards: Simplifies compliance efforts and demonstrates security best practices.
- Automated threat detection and response: Proactively identifies and mitigates security threats.
- Zero Trust architecture integration: Further strengthens security posture.
How can I get started with CyberArk?
- Visit the CyberArk website: Explore their resources, including white papers, case studies, and product information.
- Schedule a demo: Experience CyberArk firsthand and discuss your specific needs with a representative.
- Download a free trial: Evaluate CyberArk’s features and functionality in your own IT environment.
- Contact the CyberArk sales team: Discuss your specific needs and requirements with a sales representative.
Popular Courses